A Novel Intelligent AI-based Security to Enhance the Data Communication
Keywords:
Internet of things, Deep Neural network, ASCII, string value, prime numbers, MT-ECC, secure communicationAbstract
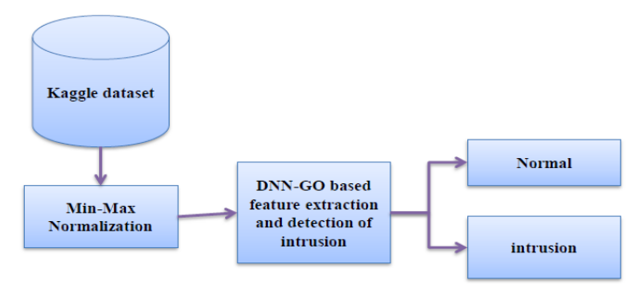
In this work, we propose a novel known as matrix translation and Elliptic curve cryptography (MT-ECC) approach for secured data communication in IoT network systems. The proposed approach includes phases such as the key generation stage, encryption stage; cluster-based secure routing stage, and decryption stage. Moreover, we introduced two types of tables such as string location relying on ASCII value and Prime number generation table and space reference table. Meanwhile, after the completion of key generation on the transmitter side, the data is transmitted to the receiver side and authorized users can access the data without any loss. Besides, if any attacks happen means it is necessary to detect the intrusion and normal data, and for that purpose we propose a novel Deep Neural Network (DNN) based Gazella optimization (GO) algorithm which effectively detects the intrusion and separates the normal data traffic from the available datasets. For the experimental purpose, we have taken the Kaggle dataset and implemented it in MATLAB and the comparative results show that the proposed approach is effectively used for secured communication and detects intrusion efficiently in case attacks happen.
Downloads
References
Niu, Z., Zhang, B., Wang, J., Liu, K., Chen, Z., Yang, K., Zhou, Z., Fan, Y., Zhang, Y., Ji, D. and Feng, Y., 2020. The research on 220GHz multicarrier high-speed communication system. China Communications, 17(3), pp.131-139.
Fortino, G., Fotia, L., Messina, F., Rosaci, D. and Sarné, G.M., 2020. Trust and reputation in the internet of things: State-of-the-art and research challenges. IEEE Access, 8, pp.60117-60125.
Shafique, K., Khawaja, B.A., Sabir, F., Qazi, S. and Mustaqim, M., 2020. Internet of things (IoT) for next-generation smart systems: A review of current challenges, future trends and prospects for emerging 5G-IoT scenarios. Ieee Access, 8, pp.23022-23040.
Do, D.T., Van Nguyen, M.S., Nguyen, T.N., Li, X. and Choi, K., 2020. Enabling multiple power beacons for uplink of NOMA-enabled mobile edge computing in wirelessly powered IoT. IEEE Access, 8, pp.148892-148905.
Dian, F.J., Vahidnia, R. and Rahmati, A., 2020. Wearables and the Internet of Things (IoT), applications, opportunities, and challenges: A Survey. IEEE Access, 8, pp.69200-69211.
Sekaran, R., Patan, R., Raveendran, A., Al-Turjman, F., Ramachandran, M. and Mostarda, L., 2020. Survival study on blockchain-based 6G-enabled mobile edge computation for IoT automation. IEEE access, 8, pp.143453-143463.
Liao, B., Ali, Y., Nazir, S., He, L. and Khan, H.U., 2020. Security analysis of IoT devices by using mobile computing: a systematic literature review. IEEE Access, 8, pp.120331-120350.
Azghadi, M.R., Lammie, C., Eshraghian, J.K., Payvand, M., Donati, E., Linares-Barranco, B. and Indiveri, G., 2020. Hardware implementation of deep network accelerators towards healthcare and biomedical applications. IEEE Transactions on Biomedical Circuits and Systems, 14(6), pp.1138-1159.
Du, Z., Wu, C., Yoshinaga, T., Yau, K.L.A., Ji, Y. and Li, J., 2020. Federated learning for vehicular internet of things: Recent advances and open issues. IEEE Open Journal of the Computer Society, 1, pp.45-61.
Liu, Y., Garg, S., Nie, J., Zhang, Y., Xiong, Z., Kang, J. and Hossain, M.S., 2020. Deep anomaly detection for time-series data in industrial IoT: A communication-efficient on-device federated learning approach. IEEE Internet of Things Journal, 8(8), pp.6348-6358.
Liu, R.W., Nie, J., Garg, S., Xiong, Z., Zhang, Y. and Hossain, M.S., 2020. Data-driven trajectory quality improvement for promoting intelligent vessel traffic services in 6G-enabled maritime IoT systems. IEEE Internet of Things Journal, 8(7), pp.5374-5385.
Singh, M., Aujla, G.S., Singh, A., Kumar, N. and Garg, S., 2020. Deep-learning-based blockchain framework for secure software-defined industrial networks. IEEE Transactions on Industrial Informatics, 17(1), pp.606-616.
Yin, B., Yin, H., Wu, Y. and Jiang, Z., 2020. FDC: A secure federated deep learning mechanism for data collaborations in the Internet of Things. IEEE Internet of Things Journal, 7(7), pp.6348-6359.
Makkar, A., Garg, S., Kumar, N., Hossain, M.S., Ghoneim, A. and Alrashoud, M., 2020. An efficient spam detection technique for IoT devices using machine learning. IEEE Transactions on Industrial Informatics, 17(2), pp.903-912.
Li, B., Wu, Y., Song, J., Lu, R., Li, T. and Zhao, L., 2020. DeepFed: Federated deep learning for intrusion detection in industrial cyber–physical systems. IEEE Transactions on Industrial Informatics, 17(8), pp.5615-5624.
Mothukuri, V., Khare, P., Parizi, R.M., Pouriyeh, S., Dehghantanha, A. and Srivastava, G., 2021. Federated-Learning-Based Anomaly Detection for IoT Security Attacks. IEEE Internet of Things Journal, 9(4), pp.2545-2554.
Zolanvari, M., Teixeira, M.A., Gupta, L., Khan, K.M. and Jain, R., 2019. Machine learning-based network vulnerability analysis of industrial Internet of Things. IEEE Internet of Things Journal, 6(4), pp.6822-6834.
Garg, S., Kaur, K., Kumar, N. and Rodrigues, J.J., 2019. Hybrid deep-learning-based anomaly detection scheme for suspicious flow detection in SDN: A social multimedia perspective. IEEE Transactions on Multimedia, 21(3), pp.566-578.
Pradeep, S., Muthurajkumar, S., Ganapathy, S. and Kannan, A., 2021. A matrix translation and elliptic curve based cryptosystem for secured data communications in WSNs. Wireless Personal Communications, 119(1), pp.489-508.
Ramesh, S., Yaashuwanth, C., Prathibanandhi, K., Basha, A.R. and Jayasankar, T., 2021. An optimized deep neural network based DoS attack detection in wireless video sensor network. Journal of Ambient Intelligence and Humanized Computing, pp.1-14.
Goldberg, S.N., Stein, M.C., Gazelle, G.S., Sheiman, R.G., Kruskal, J.B. and Clouse, M.E., 1999. Percutaneous radiofrequency tissue ablation: optimization of pulsed-radiofrequency technique to increase coagulation necrosis. Journal of vascular and interventional radiology, 10(7), pp.907-916.
Juvekar, C., Vaikuntanathan, V. and Chandrakasan, A., 2018. {GAZELLE}: A low latency framework for secure neural network inference. In 27th USENIX Security Symposium (USENIX Security 18) (pp. 1651-1669).
Agushaka, J.O., Ezugwu, A.E. and Abualigah, L., Gazelle Optimization Algorithm: A novel nature-inspired metaheuristic optimizer for mechanical engineering applications.
Otoum, Yazan, Dandan Liu, and Amiya Nayak. "DL‐IDS: a deep learning–based intrusion detection framework for securing IoT." Transactions on Emerging Telecommunications Technologies 33, no. 3 (2022): e3803.
Qiu, Han, Qinkai Zheng, Gerard Memmi, Jialiang Lu, Meikang Qiu, and Bhavani Thuraisingham. "Deep residual learning-based enhanced JPEG compression in the Internet of Things." IEEE Transactions on Industrial Informatics 17, no. 3 (2020): 2124-2133.
Alzubi, Jafar A., Ramachandran Manikandan, Omar A. Alzubi, Issa Qiqieh, Robbi Rahim, Deepak Gupta, and Ashish Khanna. "Hashed Needham Schroeder industrial IoT based cost optimized deep secured data transmission in cloud." Measurement 150 (2020): 107077.
Yu, K., Tan, L., Mumtaz, S., Al-Rubaye, S., Al-Dulaimi, A., Bashir, A.K. and Khan, F.A., 2021. Securing critical infrastructures: deep-learning-based threat detection in IIoT. IEEE Communications Magazine, 59(10), pp.76-82.
Amjan Shaik, Bui Thanh Hung, Prasun Chakrabarti, Siva Shankar S and Nikhat Parveen,”A Novel Intelligent AI-based Security to Enhance the Data Communication: An Empirical Review”, 2nd International Conference on Intelligent Systems & Sustainable Computing ( ICISSC -2022), Malla Reddy University, Hyderabad, India.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





